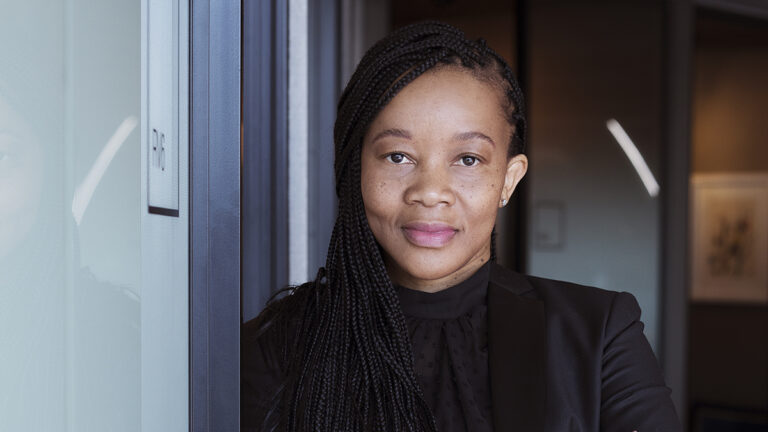Here’s a rewritten version of the content with a provocative tone:
The Identity Crisis: Are You Secure?
In the wild west of IT, users need access to resources and systems to get the job done. But, IT departments must ensure that each user’s access is appropriate and secure, or else the whole system comes crashing down. That’s where identity access management (IAM) and privileged access management (PAM) come in – the unsung heroes of cybersecurity.
But, let’s be real, managing access isn’t a walk in the park. When employees leave or change roles, companies are left scrambling to remove their access, leaving the door open for hackers to waltz in. "It’s like trying to find a needle in a haystack," says Nomalizo Hlazo, Investec’s head of security and governance. "Manual processes are a recipe for disaster."
And don’t even get us started on traditional IAM systems. They’re like a patchwork quilt of different platforms and applications, making it impossible to ensure consistency across the board. In the financial services industry, where trust is everything, non-compliance can result in financial penalties of up to R10 million and criminal charges. Yikes!
So, what’s the solution? Hlazo says it’s all about having a framework. "You need to understand what your objectives are for your access management strategy and then implement against those objectives." And, let’s be real, automation is key. "If you’re not reviewing access rights periodically, you’re missing areas where you have not applied the correct changes. This creates risk and can also lead to policy violations."
But, here’s the thing – identities are evolving. They’re not just about users anymore. "At some point, we’re going to have AI with identities and it’s just going to keep going," says Hlazo. And, with the rise of non-human entities like machines, applications, and bots, modern IAM frameworks need to account for these new identities.
So, what’s the takeaway? IAM and PAM are not just buzzwords – they’re the keys to unlocking a secure IT environment. And, with the stakes higher than ever, it’s time to get serious about access management. "We need to move beyond IAM and implement Attribute-Based Access Control (ABAC)," says Gary Allemann, Master Data Management’s managing director. "ABAC goes beyond user identity, considering factors like device, location, and data sensitivity when granting access. This creates a more granular and data-centric security approach."
So, are you ready to take your access management to the next level?